ipv6 is one of my interests and while I did have it previously on my lab network I had to let it go when I got rid of my edgerouter in lieu of an ASA. I felt obligated to switch to the ASA because of work, I grabbed a 5520 off ebay and no code existed to give it ipv6 Prefix Delegation support. I ran into a 5515-x recently that has resolved that and I was able to get an ipv6 friendly network back up and running. I just wanted to run over some stuff like configuration and decision making when dealing with ipv6. As someone who never saw the days before NAT, ipv6 is pretty much like culture shock and takes some time to adjust to. A lot of that adjustment is something that comes with use so there’s really no sense in me trying to convey it, however there are a couple key points I’ll try to highlight. Right off the bat however I would like to recommend the following podcast if you have further interest in ipv6 being implemented across an array of different use cases and business requirements.
There’s a wealth of content there that might feed the imagination and inspiration as well as cover the technical challenges when rolling out ipv6 especially in a dual stacked environment. That said, I feel a bit silly focusing on ipv6 here since I don’t consider myself that much into true “networking” at this stage in my career as compared to some of my inspirations. However, I do try to keep myself well rounded and ipv6 is a very real and valid skill today. That and within the past 6 months our Azure VM’s have been getting ipv6 addresses… Something is coming.
ipv6 PD
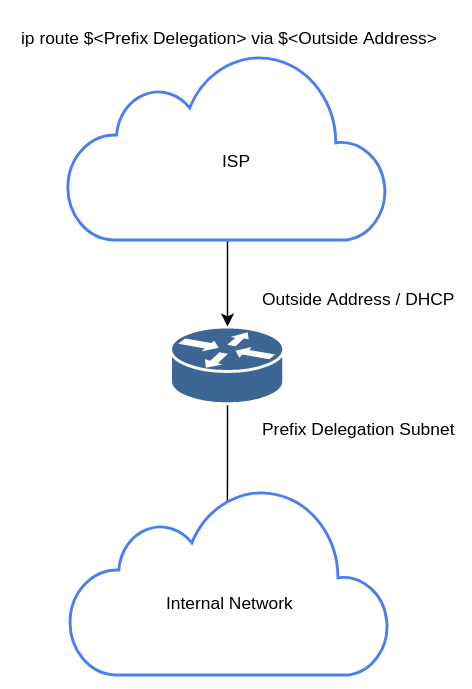
ipv6 Prefix Delegation (PD) is basically DHCP… but for ipv6. Since ip6 is intended to be used without NAT, a network doesn’t need just a single “public” IP like we see with ipv4, instead a range is assigned to each network similar to what ipv4 used to be well before my time. This range gives each host a GUA or Global Unicast Address. The typical ISP provides a requesting customer a DHCP address for the outside interface of their router/modem along with a subnet for internal use. This subnet for internal use is the PD. The ISP then assigns a route for that whole PD or ipv6 subnet with the single address assigned to the router/modem as the next hop. The PD offered can be anywhere from a /64 to a /48. The significance here is that while you can resize an ipv6 subnet to whatever you want, it’s best practice to make every subnet a /64. This even applies to P2P’s or small niche networks. The idea behind this is that, well.. you can. There’s no shortage of subnets to use. This flies in the face of modern ipv4 networking where we break subnets down into /28’s, /29’s, or even /30’s to save as much address space as possible and to be honest, this is a hard habit to break. The reason to try is break this habit however is simplicity. All ipv6 subnets should be in multiples of 4 bits. This prevents the old subnet ritual of doing binary math to determine the network and address space ID’s. Let me explain.
All assigned ipv6 prefixes should be in multiple of 4. Lets start with the smallest best practice subnet size, a /64. This looks like…
NNNN:NNNN:NNNN:NNNN:HHHH:HHHH:HHHH:HHHH
Where N is for network and H is for host
The next largest subnet would be not a /63 as it would with traditional ipv4 subnetting, but /60. a /60 looks like…
NNNN:NNNN:NNNN:NNNH:HHHH:HHHH:HHHH:HHHH
Notice that compared to ipv4 subnetting, the range is a whole integer place as compared to a range of values. This key difference is what makes some parts of ipv6, well… easy. A comparable ipv4 address would be a /15 which would look something like…
NNN.128-255.HHHH.HHH
Gone are the days of doing binary math to figure out host ranges with ipv4 addressing. The reason this is possible is again, due to the address space we have to work with. There’s no need to preserve subnets or network space. A /64, again the smallest subnet we should be seeing with ipv6, offers 18,446,744,073,709,551,616 addresses. In addition, each 4 byte hop from one subnet size to the next offers 16^(4bytehop) subnets to use. That means that a /60 offers 16 /64’s to allocate on a network. Given my residential ISP offers a PD of /60, that means I have 16 /64 networks that could have 18,446,744,073,709,551,616 addresses, or 2.951479052×10²⁰ globally unique addresses in all on a home network! The next step up, a /56 Prefix Delegation would offer 256 individual subnets with the same 18 quad zillion address space each! This changes how we approach IP space allocation completely.
The main concerns
So there’s a couple big points that stood out to me with ipv6 when compared with ipv4.
- How do we keep track of so many host on a single subnet
- How do we distribute an ISP ipv6 space within a network
So many Hosts
The first one should be pretty easy to tackle, DHCPv6. Yes ipv6 offers Stateless Address AutoConfiguration, or SLAAC . SLAAC is great for things like guest wifi networks or maybe 4G and 5G mobile networks. It allows a host to grab it’s own address on a network and get to work. The host generates it’s own address and relies on not having a collision which is not a bad strategy considering the address space we’re working with. Router Advertisements or RA’s can take care of sharing a default gateway or a DNS server. SLAAC allows the host to determine it’s own address but as a result, there’s no central management or repository of hosts on a network.
DHCPv6 stateless is similar to SLAAC in that the host grabs it’s address the same way, but the RA flags a bit to inform the host to still make a dhcp query for additional settings. The benefit here is that the DHCPv6 server can solicit network settings that RA’s and NDP can’t facilitate. Again though, there’s no record of hosts on a network because there’s no central repository of address leases.
DHCPv6 stateful is the most familiar configuration when compared to ipv4. The DHCPv6 server hands out all network configuration including address, route, dns server, etc. With this approach there’s a central point where all addresses on a network can be referenced, we can query address leases without having to scan a network to see what’s active. It’s inconceivable to scan an ipv6 /64 for hosts the same way we’ve done with ipv4 space. Having a central repository of addresses is necessary and SLAAC or DHCPv6 Stateless simply does not allow the control most are going to need over a network.
The big issue here I’ve hit on again and again is the central location to find network participants. There’s another solution to this that as we start using ip6 more and more, we may actually start seeing an implementation of. So long as network hosts are routing traffic, the router to a given subnet is a reliable source of host information. If solutions start leveraging this as a way to gain visibility into a network a DHCPv6 server might not be needed. Today though, I don’t know of any network solutions that do this.
Lastly, it’s worth mentioning static IPv6 assignment… Just as with ipv4, static assignment is still a thing among network infrastructure and servers. There’s nothing wrong with continuing to use it.
Handling a Prefix
Pulling a Prefix Delegation or PD differs from ISP to ISP and from edge device to edge device, but there’s a couple things that are common. First, many ISP’s don’t seem to take kindly to Routing Advertisements. It may be best to disable RA’s on the WAN interface of the edge device. Second, an ISP usually accepts a PD “hint” which is basically the PD size you’re requesting. A business ISP will work with a customer to provide the PD needed, but for residential most ISP’s offer either a /60 or /56. Note again that the PD is staying true to the 4 bit rule. In my case I’m using an ASA 5515-x and I have Comcast to work with. A working config looks like…
interface GigabitEthernet0/0 nameif outside security-level 0 ip address dhcp setroute ipv6 address dhcp default ipv6 enable ipv6 nd suppress-ra ipv6 dhcp client pd hint ::/60 ipv6 dhcp client pd WANPD ipv6 ospf 1 area 0
This creates an PD object called WANPD that can then be referenced by other interfaces. Also note the hint where I’m asking for a /60, the largest PD that Comcast will give me. Lastly notice that I’m not applying the PD space to the interface, instead we’re using regular DHCPv6 to assign an address and grab a default route, the PD is for use on other interfaces. An interface referencing the PD to assign an address looks like…
interface GigabitEthernet0/1 nameif inside security-level 100 ip address 172.16.99.1 255.255.255.252 ipv6 address fe80::1 link-local ipv6 address WANPD ::a:0:0:0:1/64 ipv6 enable ospf message-digest-key 1 md5 8 oXXXXXXXXXXXXXXXXXXXXXX= ospf authentication message-digest ipv6 ospf 1 area 0
Noting the line with WANPD, the ASA is referencing the PD assigned and appending the address that I’ve specified as
NNNN:NNNN:NNNN:NNN a::1/64
I can view that prefix and it’s use with…
asa# show ipv6 general-prefix
IPv6 Prefix WANPD, acquired via DHCP PD
2601:989:200:f6b0::/60 Valid lifetime 224971, preferred lifetime 224971
Consumer List Usage count
inside (Address command) 1
DMZ (Address command) 1
As well as view all DHCPv6 information on the outside interface with…
asa# show ipv6 dhcp interface outside
GigabitEthernet0/0 is in client mode
Prefix State is OPEN
Renew will be sent in 14:30:38
Address State is OPEN
Renew for address will be sent in 09:05:12
List of known servers:
Reachable via address: fe80::201:5cff:fe88:3846
DUID: 00010001179112EA14FEB5D7E727
Preference: 0
Configuration parameters:
IA PD: IA ID 0x00030001, T1 172800, T2 276480
Prefix: 2601:989:200:f6b0::/60
preferred lifetime 345600, valid lifetime 345600
expires at Aug 20 2019 02:41 AM (225038 seconds)
IA NA: IA ID 0x00030001, T1 172800, T2 276480
Address: 2001:558:6031:2e:3d29:b42f:9bb2:feb0/128
preferred lifetime 345600, valid lifetime 345600
expires at Aug 19 2019 09:16 PM (205512 seconds)
DNS server: 2001:558:feed::1
DNS server: 2001:558:feed::2
Information refresh time: 0
Prefix name: WANPD
Prefixes sent as hint:
::/60
The use of the PD make address assignment more programmatic and in the case that my ISP were to change the PD it’s assigning to me, it would automatically change to this new assignment as interfaces come up. For most circumstances this is as far as anyone is going to go with this. I need to take this prefix and push it further into my network though, my inside interface is connected to a router, not a host subnet. There’s a couple different options for this…
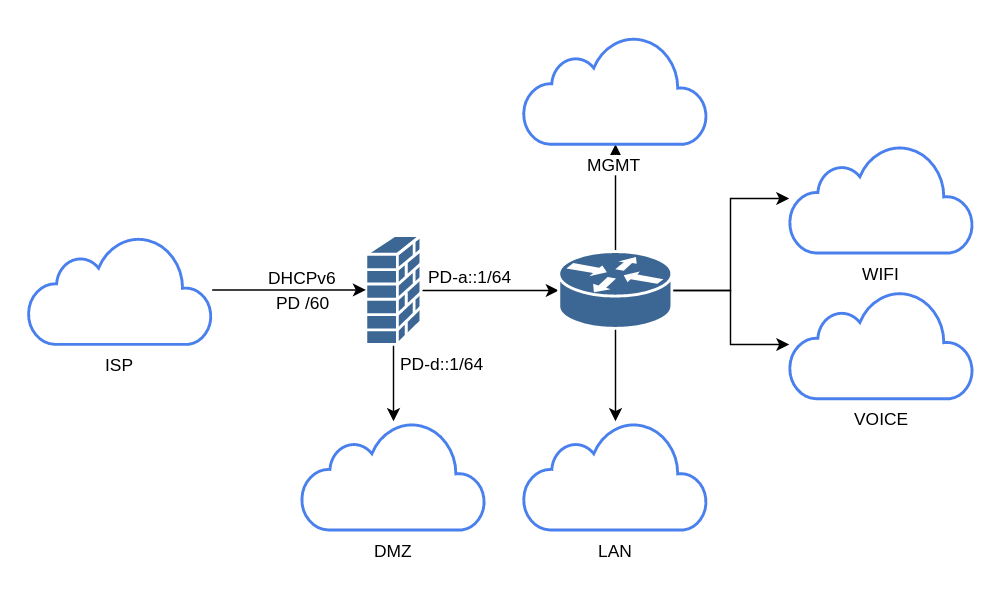
PD takes care of assigning addresses to everything off my edge device or ASA, however there’s no way to push that PD onto the next L3 device. There’s a couple options though to make things easier. I could consider using DHCPv6 and configure my ASA to hand out PD’s to hosts on it’s inside interface, in this case my router. This would allow me to assign the remaining /64’s not used by the ASA to my internal router. This would require me to break the 4 bit rule though and I’d prefer not to do that. On top of that, my internal router’s code doesn’t support PD. Instead I’ve gone with defining a general prefix on my router to make interface address assignment easier.
iOS and most network OS’s allow declaring of a General Prefix which purpose is to just make address assignment easier. Similar to PD within the ASA, it creates an object that can be referenced when assigning addresses to interfaces. At Global config, just enter…
ipv6 general-prefix LANPREFIX 2601:989:200:F6B0::/60
And then interface ipv6 addresses can be assigned with…
interface GigabitEthernet0/1 ipv6 address fe80::1 link-local ipv6 address WANPD ::a:0:0:0:1/64
While this doesn’t fully automate a PD change from the ISP, it makes it pretty painless. The real issue with PD changes from an ISP for me is ipv6 public DNS records, server ipv6 static assignments, and DHCP server settings. At least the network infrastructure isn’t such a task to re-assign. Routes are taken care of with OSPFv3 so really the only thing that needs adjustment during a change is the General Prefix on the internal router.
A few other notes
Just like ipv4 dhcp helper, ipv6 can do DHCPv6 relay. This is done on the listening interface with…
interface Vlan99 description LAN ip address 10.17.17.1 255.255.255.224 ip helper-address 10.17.17.37 ip ospf 1 area 0 ipv6 address LANPREFIX ::9:0:0:0:2/64 ipv6 nd managed-config-flag ipv6 dhcp relay destination 2601:989:200:F6B1::37 Vlan1 ipv6 ospf 1 area 0
While the managed config flag is optional, it includes a bit in RA’s that tell hosts that they are to attempt a DHCPv6 requests for more network settings. Most host won’t require this bit but it may help edge cases.
The Vlan1 on the end of the relay line is also not required, it’s just where we can specify the interface that the DHCPv6 server can be found on.
Remember that routes are not defined in DHCPv6, ipv6 relies on RA’s for this so ensure all inside interfaces don’t disable them.
It’s also possible to request more than just the PD length on most devices. Most allow requesting a specific Prefix itself. For residential it’s possible to edit your interface config to specify the PD once you get one the first time in an effort to retain that one on reboots/bounces. Unfortunately my provider does not honor these requests. The ASA for instance would like like..
ipv6 dhcp client pd hint 2601:989:200:f6b0::/60 instead of... ipv6 dhcp client pd hint ::/60
Mind the firewall. Don’t rely on NAT for security because well.. it’s gone. NAT should have never been relied on for security in the first place as that’s not what it was designed to solve but we’ve all come to rely on it. That habit dies fast with ipv6.
